
Penetration tests allow a company to see its cybersecurity vulnerabilities from a cybercriminal’s perspective, while vulnerability scanning is software that finds and patches cybersecurity vulnerabilities. Both are important components of an overall vulnerability assessment and we recommend doing both often, starting with a vulnerability scan.
With this in mind, let’s take a look at the similarities and differences between penetration testing and vulnerability scanning, including how to use them together as part of your ongoing security assessment:
Guide To Penetration Testing Vs. Vulnerability Scanning
Vulnerability scanning is cybersecurity software that scans for vulnerabilities within a company’s IT infrastructure.
“Vulnerability scanning technology can help you identify potential weak points in your software, so you can take steps to fix them before they’re exploited,” said Abu Bakar, co-founder, Coding Pixel, a Los Angeles-based software development company.
“By identifying and addressing vulnerabilities before they can be exploited by hackers, penetration tests help reduce the risk of data breaches and other cybersecurity issues.”
A vulnerability scanner can identify and create an inventory of a company’s systems, such as servers, desktops, laptops, virtual machines (VMs), containers, firewalls, switches, and printers connected to a network.
Vulnerability scanners will attempt to log in to systems to build a visual scan of the system. The result of a vulnerability scan is focusing on any known vulnerabilities within a network and patching them.
See more: What is Vulnerability Scanning & Why Should You Do It?
In vulnerability scanning there are multiple steps including getting access, reporting, fixing problems, and verifying that the scan was efficient. If a vulnerability scanner tends to find more problems in one area, it will heavily focus on future and past vulnerabilities in the area. A user can choose which areas are most important to the company.
Vulnerability scanners follow multiple steps in their execution process:
See more: Simple Guide to Vulnerability Scanning Best Practices
Once the steps have been completed, the company will receive a report.
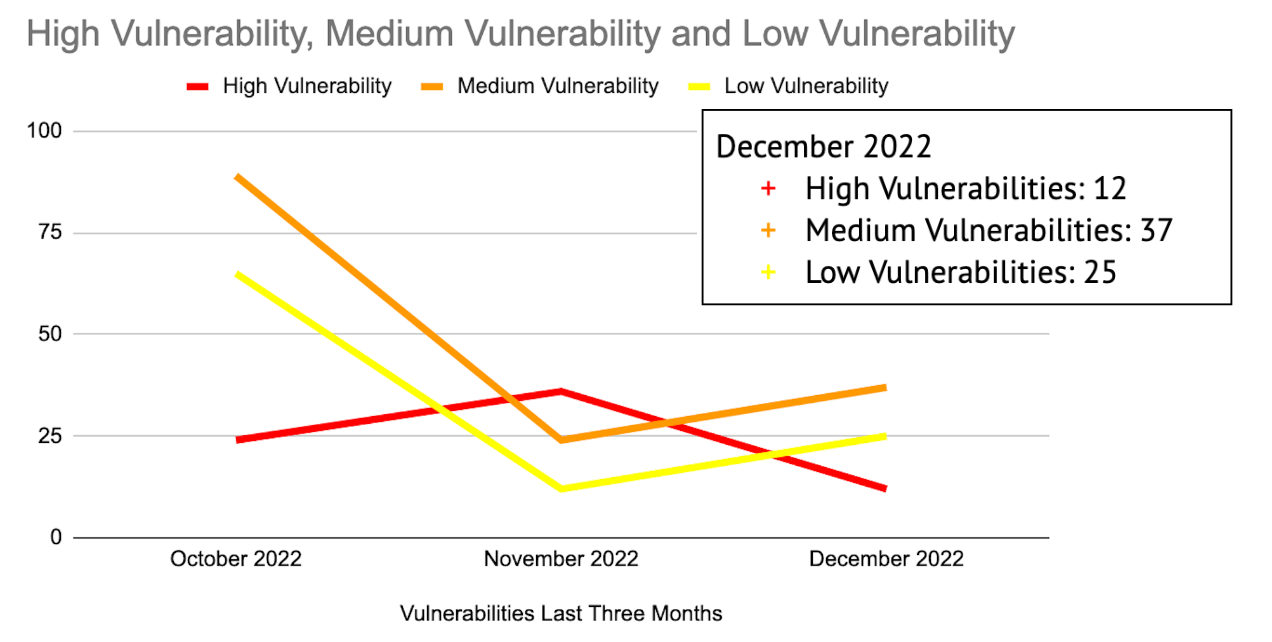
When looking at the vulnerability scanning report, you may notice the timeline and varying numbers across the chart. The chart goes over three months: October, November, and December.
Throughout the report you will notice the numbers vary as vulnerabilities are higher at different points of the months.
The red line is high vulnerability, the orange line is medium vulnerabilities, and the yellow line is low vulnerabilities. The box over the chart is the vulnerability count for December in each category. This helps a company see what needs to be fixed immediately, and what they can take more time on.
See the chart below:
Many technology companies have created their types of vulnerability scanning. From Microsoft to AWS, vulnerability scanning tools may provide help to your company. These are some of the top vulnerability scanning software in the market:
Scanning and ensuring the vulnerabilities are remediated helps lower the odds of an organization’s overall risk exposure from cyberattacks by exposing any weaknesses.
Using vulnerability scanning is an important part of creating a cybersecurity strategy and can save company’s time, money, and vital data. Some of the other benefits include:
See more: Why Vulnerability Scanning is Important
A penetration test is an intentional cyberattack against a company’s network and computer infrastructure to find their vulnerabilities.
“Penetration testing is a vital part of a critical infrastructure assessment that allows all parties to assess risks and implement cybersecurity mitigations and standards,” said Matt Morris, managing director, 1898 & Co., a Kansas City-based consulting firm focused on cybersecurity.
Penetration tests use the “tools, techniques, and processes” of cybercriminals to find and demonstrate how hackers find a company’s weaknesses, according to a post by Synopsys, which provides application security software.
“A penetration test is a hands-on exercise,” said Ray Canzanese, director, Netskope Threat Labs, a cybersecurity company focused on cloud, data, and network security.
“A team of attackers is given rules of engagement and tasked with finding their way into protected information systems. Penetration testers might use software to automate parts of the process, but unlike vulnerability scans, penetration tests cannot be automated.”
Penetration tests can examine whether a system is strong enough to handle cyberattacks from multiple positions. Most penetration tests can look into any aspect of a company’s infrastructure.
See more: What is Penetration Testing?
Penetration testing allows ethical hackers to analyze the infrastructure, find what the infrastructures are safe and unsafe, and find the strategy and tools to break into the network. The penetration testing process breaks down to four steps: Planning, scanning, gaining access, and analysis.
See the steps below for further information:
See more: Penetration Testing Phases & Steps Explained
When the penetration test is completed, a company will receive a report that explains every vulnerability.
A penetration test result will most likely come from a third-party provider. The report will break down the vulnerabilities one by one from the impact, risk, likelihood, and fix. They are rated by low, medium, and high.
The penetration test professional will also supply a summary of the risk and the affected assets. The report will most likely look like this:
While conducting the penetration test of the network, the following vulnerability was found:
| Impact | Risk | Likelihood | Fix |
|---|---|---|---|
| Low | High | High | Medium |
Summary of Risk:
X identified the application is vulnerable to a process flaw that allows an attacker to enter by social engineering tactics.
Affected Assets:
X application, websitename.com
Many technology companies have created their own penetration testing tools. From Acunetix to Rapid7, penetration testing tools may provide help to your company. These are some of the top penetration testing tools in the market:
A penetration test is one of the best cybersecurity tools to expose vulnerabilities and weaknesses in your infrastructure. Having the ability to find vulnerabilities is vital to ensuring that a company’s data is as secure as it needs to be.
See below for more benefits about penetration testing:
Penetration tests and vulnerability scans are compared often, but many companies may not know why. While they both detect vulnerabilities and cybersecurity threats, they are different. From the way the systems are scanned and tested, to the end result of these scans and tests.
See below for the differences between Penetration tests and vulnerability scanning:
| Vulnerability scans | Penetration tests |
|---|---|
| Finds and measures vulnerabilities in infrastructure, such as outdated protocols, certificates, and services | Finds vulnerabilities and exploits them to take advantage of the company’s infrastructure |
| End result is a list of vulnerabilities prioritized by severity | End result charts the vulnerabilities that can be taken advantage of |
| Recommended when system has known security issues or if a security issues have not been found | Recommended for companies with strong security systems, but still want to find hidden vulnerabilities |
| Concerned with finding as many vulnerabilities as possible | Concerned with discovering vulnerabilities that can be exploited |
| Vulnerability scan is automated | Penetration test requires a cybercrime expert to direct the intentional cyberattack |
| Vulnerability scanning requires continuous scans | Penetration tests do not need to be conducted as often |
Experts recommend doing a vulnerability scan as well as a penetration test as part of a broad vulnerability assessment.
“Vulnerability scanning and penetration testing are two methods for monitoring an organization for potential threats and security gaps,” said Chad Peterson, managing director, NetSPI, a Minneapolis-based cloud cybersecurity company.
“Both techniques, while different, are an important part of a well-run penetration test and ongoing offensive security program.”
While vulnerability scanning helps give a company a baseline of their cybersecurity weaknesses, adding penetration testing can enable another layer of tested network security.
See more: Penetration Testing vs. Vulnerability Testing: An Important Difference
Penetration tests allow a company to see their cybersecurity vulnerabilities from a cybercriminal’s perspective, while vulnerability scanning is software that finds and patches cybersecurity vulnerabilities.
Vulnerability scanning and penetration testing are important, because they help a company understand the cybersecurity risks within their IT infrastructure.

Datamation is the leading industry resource for B2B data professionals and technology buyers. Datamation's focus is on providing insight into the latest trends and innovation in AI, data security, big data, and more, along with in-depth product recommendations and comparisons. More than 1.7M users gain insight and guidance from Datamation every year.
Advertise with TechnologyAdvice on Datamation and our other data and technology-focused platforms.
Advertise with Us
Property of TechnologyAdvice.
© 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this
site are from companies from which TechnologyAdvice receives
compensation. This compensation may impact how and where products
appear on this site including, for example, the order in which
they appear. TechnologyAdvice does not include all companies
or all types of products available in the marketplace.